
Why are gambling platforms targeted?
In today's digital environment, neither a small family business nor a large international gaming company is completely immune to cyberattacks. Online businesses are vulnerable to hacker attacks, and large companies are especially popular targets because they not only have rich financial and data resources, but once operations are interrupted, such as during the World Cup, users are unable to access betting platforms, recharge or withdraw cash, which will cause huge economic losses. .
But direct economic losses are not the only consequence. Players' personal data can be compromised, and hackers who gain access to a player's account can compromise their email or social media accounts, conduct blackmail, or sell the data to other malicious actors. The gaming industry frequently suffers from such cyber attacks, which increase by approximately 1000% annually, resulting in average losses for gaming operators of 31010,000 pounds. In September 2023, MGM suffered a large-scale cyber attack, forcing it to Shutting down some systems across the United States cost approximately $1 billion and took a month to resume normal operations. This shows that gambling platforms must take cyberattacks seriously, especially gambling operators that rely mainly on online business.
Sources of cybersecurity threats
The Internet is full of people whose presence on the network is not necessarily directed to a specific person or website. Hackers frequently scan the entire Internet looking for exploitable vulnerabilities and opportunities, and their goals are extremely broad and not specific. Some industries have become the focus of hackers due to their special nature, such as the fiercely competitiveiGamingonline gambling industry. Competition among peers is not uncommon, and some platforms even resort to suppressing competitors, especially during major international events.
Not only are black hat hackers threatening network security, white hat hackers (ethical hackers) are also on the rise. Their goal is to help companies fix vulnerabilities before they are exploited. Although they usually mean well, sometimes they may exploit known vulnerabilities to launch attacks if they are not duly rewarded.
Common types of cyber attacks
- 端口扫描攻击: Hackers send a set of port scan messages to try to break into a computer and learn what type of services it provides. Scanning ports to find vulnerabilities and access the system is like a thief trying each door handle. Common attack ports include8080、21、22Etc. Scanning methods includeTCP connectscanning,TCP SYNScanning, etc.
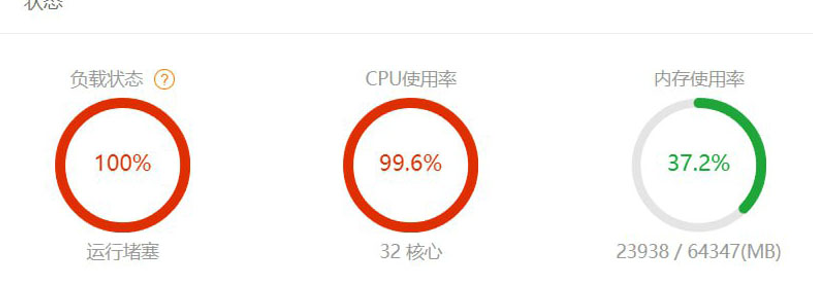
- DDoS攻击: Attackers overload the target server with a large amount of traffic, making it impossible for users to access the gambling platform. Solutions include distributing network and server resources, using firewall rules andCDN。
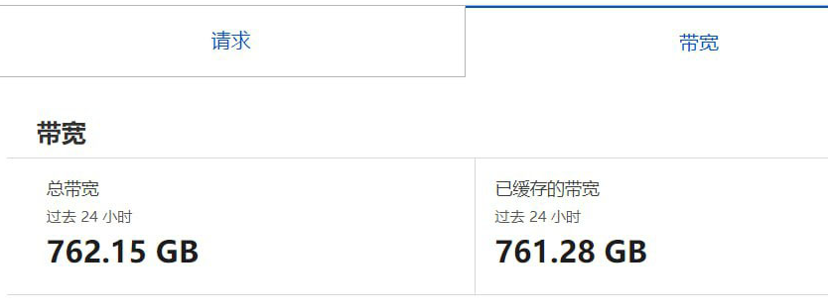
- CC攻击: Use continuous connection requests to form a denial of service attack, causing server resources to be exhausted. Countermeasures include changingWebPort, ShieldIP,useCDNwait.
- SQL注入攻击: Hackers insert maliciousSQLCommand manipulation of the database may lead to sensitive data leakage or modification of important data. Defense methods include using the latest database version, regularly backing up the database and managing permissions.
- MITM攻击: Hackers can eavesdrop on the interaction between two parties by intercepting and tampering with communication data. Defense measures include using strong encryption orVPN。
- 网络钓鱼攻击: Attackers send credible-looking emails to trick targets into providing sensitive information. Raising employee awareness is key to defense.
- 勒索软件: Malware locks the operating system, making it inaccessible unless a ransom is paid. Defenses include regularly backing up data and keeping systems updated.
- 密码攻击: Hackers gain access by guessing or intercepting passwords. Using complex passwords and multi-factor authentication are effective defense measures.
- URL猜测/解释: Hackers modifiedURLAddress access to sensitive data. Defense measures include using secure authentication and the latest encryption technologies.
- DNS欺骗和劫持: Hacker changesDNSlogs, redirecting users to fake websites. Defenses include using secureDNSConfiguration and MonitoringDNSVariety.
- 跨站脚本攻击(XSS): Hackers inject malicious scripts into web page content to steal user data or spread malware. Defenses include using safe coding practices and filtering input.
- 鱼叉式网络钓鱼攻击: Highly targeted phishing attacks, where attackers design emails based on the target's personal information. Defense measures include strengthening employee training and using multi-layered security measures.
Measures to ensure the security of gaming platforms
- 保持软件最新: Install software updates and security patches in a timely manner to prevent vulnerabilities from being exploited.
- 确保员工接受过培训: Improve employees’ ability to identify and respond to cyber threats and prevent security vulnerabilities caused by human errors.
- 选择可靠的包网公司:Choose a strong and reputable network package company to ensure the stability and safe operation of the platform. A professional network package company has a strong technical team that can quickly respond to and solve network attack problems to ensure the security of the platform.
Summary
Network security is crucial to online gambling platforms, and choosing a professional and reliable outsourcing company is the key to ensuring the stable operation of the platform. By keeping software updated, training employees, and choosing reliable technical support, gaming platforms can effectively defend against various cyber attacks and protect corporate interests and user data security. In this highly competitive industry, only by maintaining a high degree of vigilance and professional defensive measures can the continued success and development of the platform be ensured.









